Enforcing Security Between BLE-Supported Devices
The need for security
Consider two devices without a security mechanism between them. At any point during the communication of data between the two devices, a third device could come between them without authorization or detection. In BLE, the main security issues are passive eavesdropping and man-in-the-middle (MITM) attacks.
Passive eavesdropping
In this attack, a third device listens in to the data being exchanged between the two paired devices. BLE overcomes this by using AES-CCM cryptography to encrypt the data being transferred.
While AES encryption is very secure, the key exchange protocols that BLE uses can introduce some severe security issues which could allow an attacker to decrypt the shared data. The method by which the keys are exchanged, referred to as pairing, greatly affects the security of the connection.
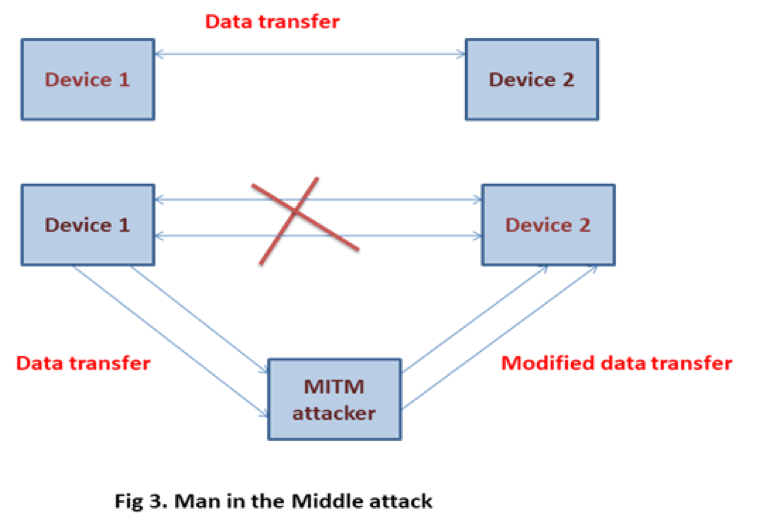
Man-in-the-middle attack
This type of attack is a security threat in which an attacker relays or alters the data communicated between the devices. The devices, however, believe that they are communicating normally and directly with each other.
Again, BLE overcomes this by using AES-CCM cryptography to encrypt the data being transferred.
Thus, the main factors in securing any connection, wired or wireless, are protecting the data and preserving confidentiality. In BLE, three main security-oriented concepts are authentication, encryption and bonding.
Authentication
Authentication is the method of verifying that the identity of a device is what that device claims it to be. With a BLE-supported door lock, for example, the lock is protected by a secret key, known as a passkey. To unlock the door, users enter the passkey to prove to the lock that the device is indeed theirs.
Encryption
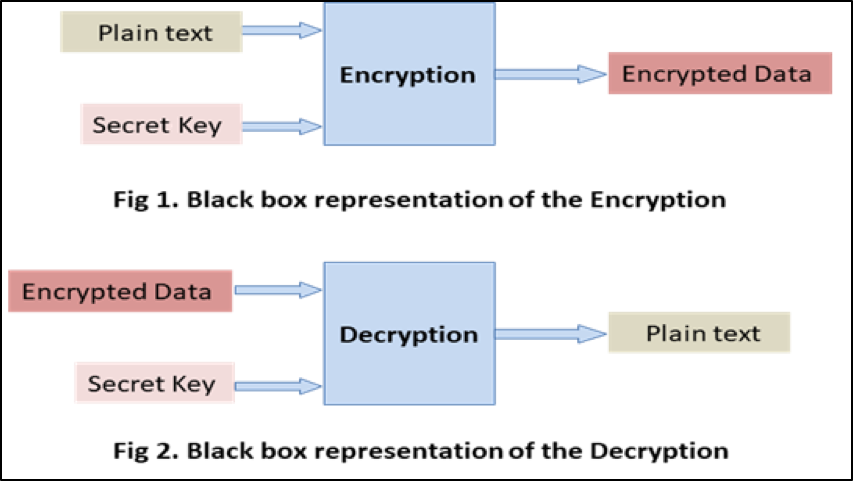
Encryption is the method of encoding data or information so that only authorized devices can understand it. In encryption at the initiator, the initiating device encrypts the data using the secret key, and then the data is transferred. In decryption at the responder, the responding device decrypts the data using the same secret key —previously shared — and then decodes the data.
Bonding
Bonding is a feature wherein the secret keys are stored in a local database on each device. Whenever the devices are close to each other, specific keys are picked from the local database to authenticate them. The devices exchange information about their respective capabilities to determine the authentication mechanism they will perform.
For more information, consult the Bluetooth core specification 5.0.
